
Cybersecurity is not merely a shield against threats; it's a strategic investment that fortifies your organization's resilience, enabling growth and innovation in an increasingly digital world.
Our Services
-

Data Protection and Recovery
Secure your business-critical information across on-premises and cloud environments.
Rapid backup, continuous monitoring and tested recovery ensure minimal downtime and data loss.
Stay compliant, resilient and prepared for any disruption. -

Account, Audit and Access Management
We assess your access controls and account activity to detect weak spots, audit anomalies and optimise your user & system access fabric.
With strong MFA, context-based access policies and continuous audit streams, you’ll have full visibility, governance and cyber-resilience. -

Network Infrastructure Management
Network security is a constantly changing environment that necessitates regular re-evaluation of architecture diagrams, configurations, access controls, and allowed traffic flows. we reassess current configurations. of devices such as physical and virtualized gateways, firewalls, wireless access points, routers, and switches.
Our Services
-
Cybersine actively manages (inventories, tracks, and corrects) all enterprise assets—end-user devices (including portable and mobile), network devices, non-computing/IoT devices, and servers—connected to the infrastructure physically, virtually, remotely, and those within cloud environments. We ensure accurate knowledge of the totality of assets that need to be monitored and protected within the enterprise. This comprehensive approach supports identifying unauthorized and unmanaged assets for removal or remediation.
-
Cybersine establishes and maintains a comprehensive incident response capability, encompassing policies, plans, procedures, defined roles, training, and communications. This proactive approach prepares your organization to detect and swiftly respond to cyberattacks. By implementing structured response protocols, we minimize damage, reduce recovery time and costs, and mitigate associated risks.
-
Cybersine establishes and maintains a comprehensive security awareness program to influence behavior among your workforce, ensuring they are security-conscious and properly skilled to reduce cybersecurity risks. Our program includes policies, plans, procedures, defined roles, training, and communications to prepare, detect, and quickly respond to attacks. We focus on educating employees to recognize social engineering attacks, implement authentication best practices, handle data securely, and identify and report security incidents. By addressing the human element, we strengthen your organization's overall cybersecurity posture.
-
Cybersine establishes and maintains comprehensive network monitoring and defense processes to proactively identify and mitigate security threats across your enterprise's network infrastructure and user base. We implement advanced tools and practices to continuously monitor network traffic, detect anomalies, and respond swiftly to potential incidents. Our approach ensures that your network defenses are not only effective but also adaptive to evolving threats, providing robust protection against cyber adversaries.
SOC Incident Response
-

Preparation (Pre-Incident Setup)
Cybersine establishes and maintains comprehensive network monitoring and defense processes to proactively identify and mitigate security threats across your enterprise's network infrastructure and user base. We implement advanced tools and practices to continuously monitor network traffic, detect anomalies, and respond swiftly to potential incidents. Our approach ensures that your network defenses are not only effective but also adaptive to evolving threats, providing robust protection against cyber adversaries.
-
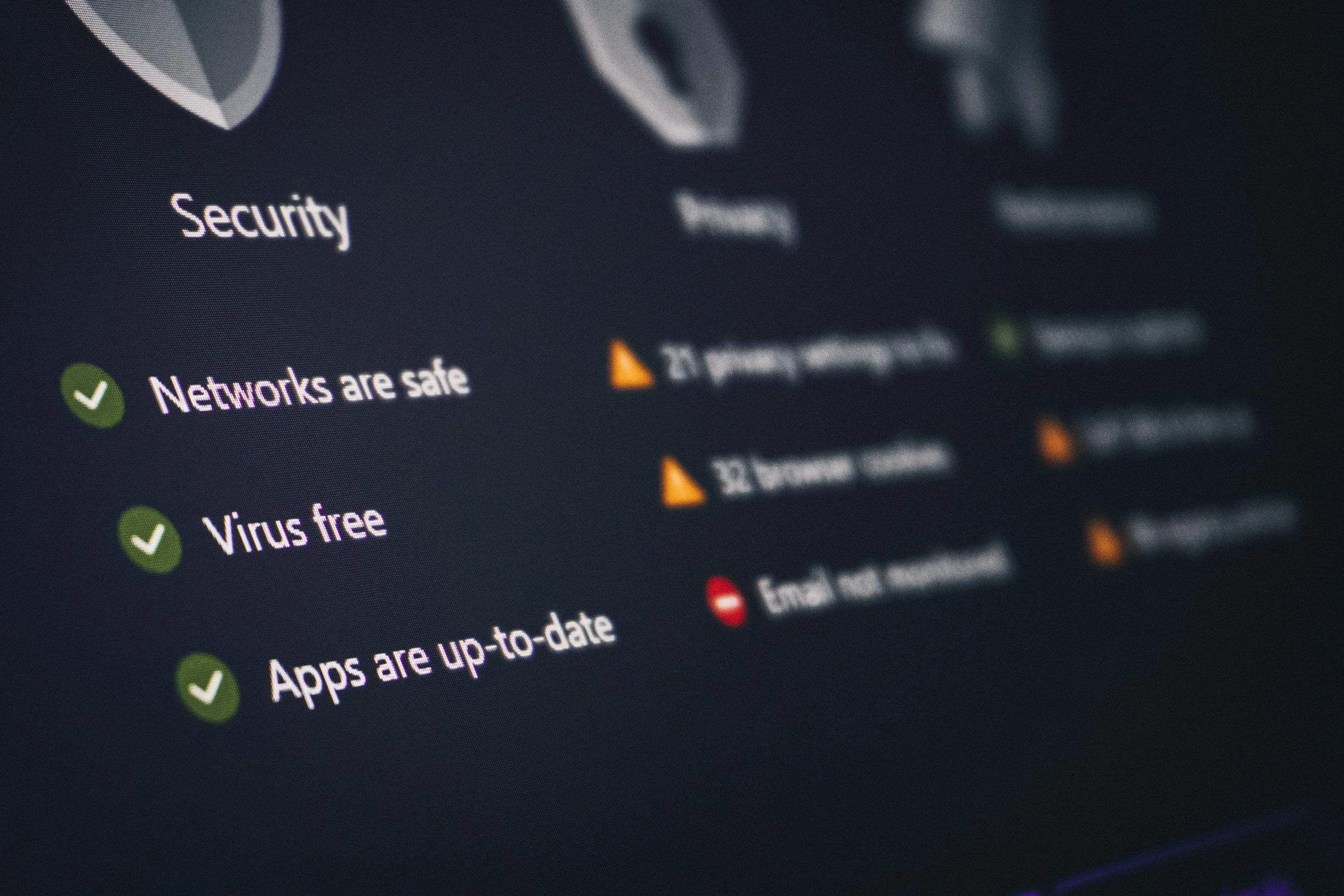
Detection & Analysis
Cybersine rapidly identifies and analyzes ransomware activity by confirming incidents through EDR alerts, ransom notes, or encrypted file extensions. We isolate affected hosts using network disconnection or EDR containment, identify the specific ransomware strain via ransom notes or file hashes, and analyze system logs and behaviors to trace execution sources, lateral movement, and detect suspicious tasks or services. Our approach maps observed behaviors to MITRE ATT&CK techniques such as T1486 (Data Encrypted for Impact), T1059 (Command Execution), and T1021.002 (SMB Lateral Movement) to understand and mitigate the attack.
-

Containment
Cybersine swiftly isolates and mitigates ransomware threats by disconnecting affected systems via network controls or EDR tools, disabling compromised accounts to prevent lateral movement, blocking external communications to halt command-and-control (C2) activities, and capturing forensic snapshots of impacted systems for detailed analysis.
-

Eradication
Cybersine systematically removes ransomware threats by deleting malicious files, scripts, and scheduled tasks, patching exploited vulnerabilities such as RDP, SMB, and outdated software, performing comprehensive antivirus/EDR scans across all affected systems, and validating the removal of persistence mechanisms like registry keys, startup items, and services to ensure a secure and clean environment.
-

Recovery
Cybersine facilitates a structured recovery process by restoring data from verified clean backups, rebuilding systems lacking secure backups, and monitoring restored systems using SIEM and EDR tools to detect any signs of reinfection. We also reset passwords, particularly for privileged and affected users, to eliminate potential access points for attackers.
-

Reporting
Cybersine conducts a comprehensive post-incident review to analyze the root cause, initial access methods, and response efficiency. We enhance detection capabilities by updating SIEM and EDR correlation rules, document detailed findings including indicators, affected systems, and timelines, and share Indicators of Compromise (IOCs) internally and with threat intelligence communities, as permitted, to strengthen future defenses.


